Internet of Trust: Your VPN is just another network

In this today post I want to address the usage of VPN for Internet connectivity. So to be clear we are not talking about a VPN to access private network such as company Intranet applications not accessible over internet.
Those past years we’ve seen a rise in VPN services for consumer and especially all of those annoying ads of VPN services that want you to absolutely buy their -85% yearly subscription. I’ve been also ask from time to time if it was recommended to use a VPN for Security reason while travelling. So in this article I want to address the Security of The Internet and if VPN is good for it. Spoiler alert, in regard of Internet, VPN does not bring that much security.
The Evolution of Internet Security
Before HTTPS
Do you remember in your childhood listening conversation on the house landline by just connecting a new phone on the copper cable? That is how easy it is to intercept non-encrypted traffic over Internet.
The HTTPS Revolution
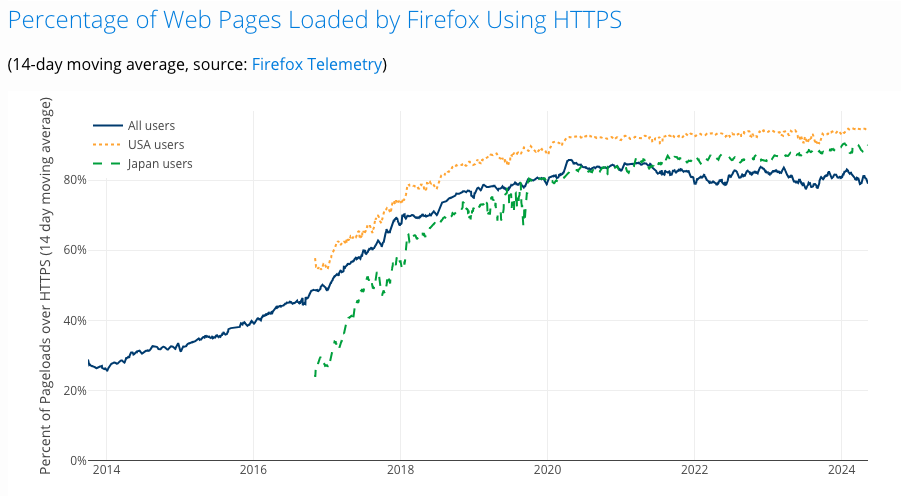
The game changed with HTTPS. Let’s Encrypt arrived in 2015 and has massively pushed the adoption of web encryption by
providing Free SSL certificate vs paying $100 a year for it. Since its inception, it has issued over 400 millions certificates!
Today 81% of global and 94% of US traffic is encrypted, safeguarding data from middlemen
Core Components of Internet Connectivity and Trust
Understanding the Internet's Structure
The Internet is a vast and intricate network composed of interconnected providers that communicate via the TCP/IP protocol. It spans across continents, with regional entities like ARIN (American Registry for Internet Numbers), RIPE (Réseaux IP Européens), and APNIC (Asia-Pacific Network Information Centre) managing the distribution of IP addresses. Every device connected to the Internet is assigned a unique IP address, which is used to route information globally through the Border Gateway Protocol (BGP). BGP acts as the Internet's postal service, ensuring that data packets are delivered efficiently from one network to another
The Role of ISPs and National Differences
Internet Service Providers (ISPs) are the backbone of Internet connectivity, but trust levels can vary significantly by geography. In the West, encrypted data transmission is the norm, making eavesdropping by ISPs challenging. However, in regions with strict censorship, like China, the landscape is drastically different. Heavy surveillance and state-imposed restrictions create a unique and often constrained online experience. This disparity highlights the importance of understanding the role and reliability of your ISP, as well as the broader national context, in ensuring secure and unrestricted Internet access.
Can you trust your Internet Service Provider?
ISPs are interconnected together similarly to highway is built and maintained, when the data hit the road it would be the operator that run and maintain the link that is responsible to securely transport it to the next junction (aka next ISP).
Some ISPs are more trustworthy than other, and some of them can be compromised, ultimately loosing a bit more trust. That’s what happened to Orange in Spain when hacker compromised their RIPE account, and of course they do not had any MFA on it. That’s crazy! secondly what’s the most funny is how hacker found it, by browsing a list of some email / password breached accounts and notice the password « ripeadmin » which provide him strong insight about what was the nature of the account.
But I have to say that I’m not even surprised anymore, most of the people in enterprise lack of sensibility to protect access to account, (Hello solarwinds123 🥲)
Deep Dive into the Components of Network Security
There is an adage in IT when a connection is not working and can’t be explained, then it has to be a DNS issue. It may be because DNS is the most distributed system on the planet (and space now)
There is so many domain resolver that relay and cache the resolution that it can be Spoofed pretty easily. By default, the DNS server used to resolve the domains are the one pushed by the ISP. For more deep dive on how DNS works see my article DNS 101. What it is and how it works
Lot of provider implement censorship on domain resolution, such as China Telecom that will spoof the IP resolution for a lot of banned domain such as github.com or proton.me
Implementing DNSSEC for Enhanced Security
To protect against DNS spoofing, implementing DNSSEC (Domain Name System Security Extensions) is crucial. DNSSEC adds a layer of security by enabling DNS responses to be verified for authenticity. It uses cryptographic signatures to ensure that the data received from a DNS query has not been tampered with and is from a legitimate source. By deploying DNSSEC, organizations can significantly reduce the risk of DNS spoofing attacks, enhancing overall network security and maintaining the integrity of their online services.
BGP and Its Security Challenges
BGP stands for Border Gateway Protocol, also known as the postal service of the Internet, directing data by finding efficient routes. However, it's not foolproof, BGP hijacking can reroute traffic maliciously, a significant security concern highlighted by numerous incidents each year.
BGP is Trustless by design, each peer can announce the management of an IP block range without being specifically the one managing it. Hopefully it’s not anybody that can be an Autonomous System (AS). But if you compromise and take control of an AS, the attacker can announce the ip prefix of a victim, forcing all the neighbour nodes to send the traffic to that AS instead of the original one managing it.
From there the attacker could do a more advance attack by being the Middle Man and routing the traffic to the original AS but listening all the communication in between. Or even null-route the traffic to do a Denial Of Service (DoS) attack. The beauty of it, the traffic would still be encrypted end-to-end.
But most of the time, the origin of a BGP hijacking is unintentional and due to a technical misconfiguration. I’m writing this the 13 of January 2024 and there is already 50 BGP incident this year detected by Cisco BGPStream that monitoring hijacks, leaks, and outages in the Border Gateway Protocol.
Does a VPN Improve the Internet security?
So by now you should understand a bit better how the Internet is working, now we can reflect on if VPN improve Internet security? And protect of us of those BGP routing incident. Ultimately, it depend from which network to what destination?
What is a VPN? it’s a private encrypted tunnel between two distinct connection. If you are connected to Internet through China Telecom, there is a lot of chance that you are not feeling protected enough and not happy with the censorship applied restricting you to access Youtube or other mainstream social media. When you established a VPN connectivity to an online Server, your internet activity will go to the Tunnel.
But you will have to trust first the company that run the VPN Service and then the ISP they are using to connect to Internet.
Now let say you are on vacation in another country, and you are restricted to view some Video because due to the country you are. You can use a VPN that will encapsulate the traffic and route you to another ISP in an authorised country.
But in terms of Security what does it change? The server that host the video will see the VPN server as the client and not the Internet connection where your computer is connected too, we could argue that improve your Privacy (as long as the VPN does not share the source IP), in the consent of handing over all of that to the VPN Service you are using.
But it does not genuinely improve the “Internet” security.
If there is a BGP routing hijack that concern the route that is connected to the VPN Service you can still face some **man-in-the-middle attack **where your data could be stolen.
To illustrate that, I made this following schema with real AS of the attack that occurs in 2022 to redirect traffic of cryptocurrency platfrom Celer Network to rewrite transaction recipient to a wallet controlled by the attacker.
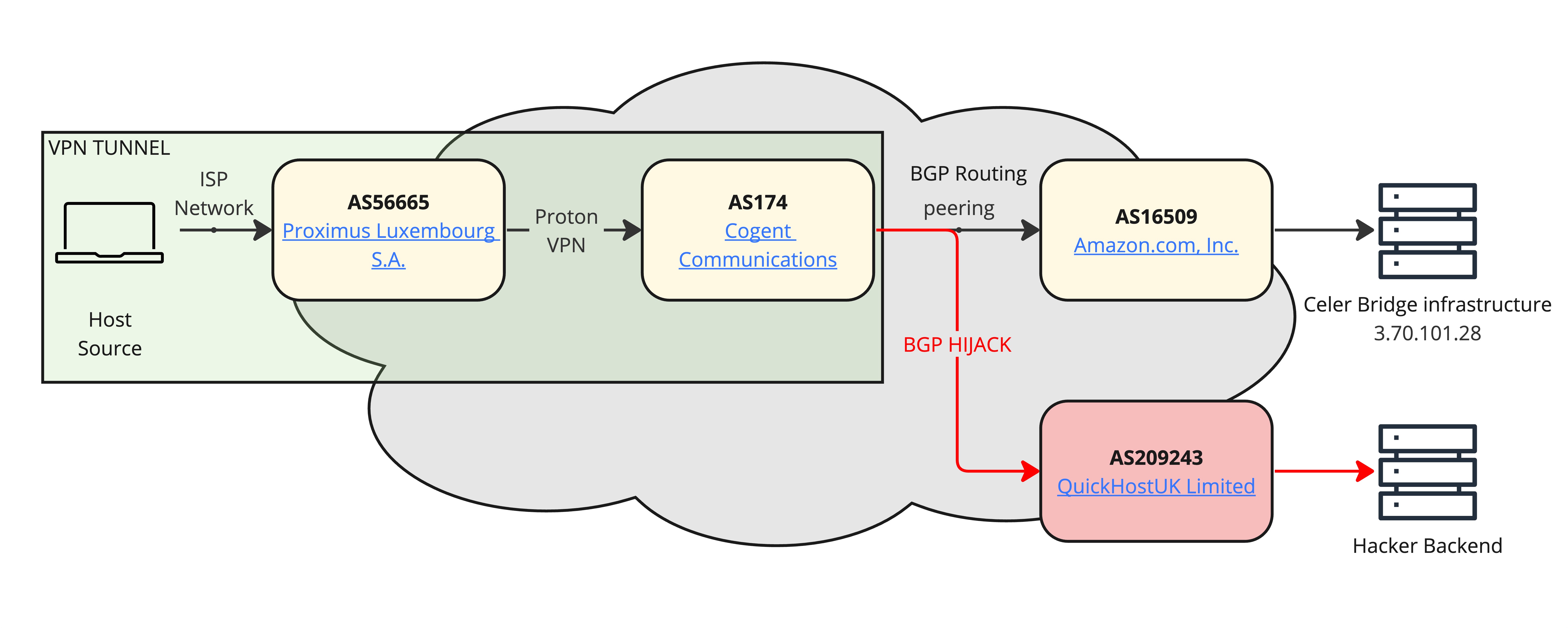
Strengthening BGP Hijacking Prevention
While I mentioned some incident regarding BGP, it's important to mention that the global community is making effort to adopt Resource Public Key Infrastructure (RPKI) in preventing BGP hijacking. RPKI helps secure BGP routing by verifying that IP address block holders are authorized to announce them, effectively mitigating unauthorized BGP announcements. Emphasizing RPKI's implementation can lead to significant improvements in securing internet routing and building a more trustworthy internet infrastructure.
In addition to RPKI, BGPsec plays a vital role by securing the path information in internet routing. BGPsec ensures the authentication of the entire AS path, preventing alterations and unauthorized diversions by malicious entities.
Conclusion
Having a VPN is just a way to use another network Autonomous System (AS) for Internet traffic. It useful if you move a lot and cannot trust or need to bypass censorship of the ISPs where you are connected to. But then you have to trust the ISPs managing the VPN. Otherwise you are just feeding your privacy data to someone else. The VPN is not solving any BPG hijacking as you will probably go through it via the peering connectivity.
The level of encryption of HTTPS website is similar to the encryption of a VPN tunnel, therefore the pure benefit of security is limited if you have the same level of trust between the two ISP.

