Uber hack explained: Simple but effective

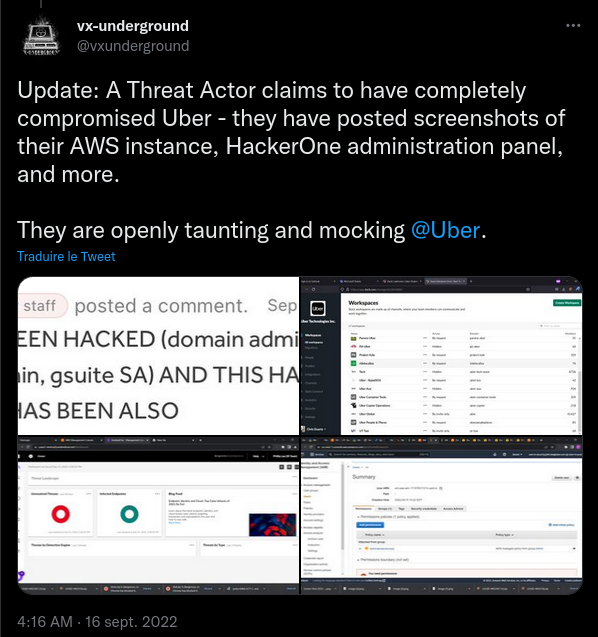
On September 16, 2022, screenshots emerged on Twitter showing that Uber's administrative accounts had been compromised. The hack was claimed by an 18-year-old security researcher, who revealed that they had gained access to Uber's systems by stealing employee passwords. From there, the hacker was able to gain access to the following major administrative panels:
- Google Apps Admin account (which contained 1.11PB of data)
- AWS uber-ts-prod account ( Public Cloud Provider )
- Sentinel One ( Cyber Security Platform to monitor and manage threat response )
- Slack ( Company Communication Platform )
- Uber's internal financial information
- The ability to administer vmware virtual machines
This hack was a major breach for Uber and serves as a cautionary tale for the importance of strong security practices.
How does it start?
It is unclear how the attackers obtained the passwords that allowed them to access Uber's systems. However, the security community on Twitter has suggested that the passwords may have been obtained through malware such as RedLine, which could have been installed on employee computers.
Another possibility is that the passwords were obtained through a third-party actor who was selling stolen passwords on the Dark Web.
It is also worth noting that the recent hack of password manager LastPass, which occurred in August 2022, may have played a role in the Uber hack. It is possible that the hackers used the stolen LastPass backups to target high-profile targets like Uber, as the Password URL from the vault was not encrypted.
MFA ByPass
Despite the fact that Uber requires multi-factor authentication (MFA) to log in to its systems, the attackers were able to gain access by obtaining employee passwords. They then attempted to "MFA bomb" the employee, repeatedly trying to log in to the account in the hope that the employee would accidentally approve the connection. This tactic, which is also known as "MFA bombing," is often successful at night when people are asleep and may not be paying close attention to notifications.
In this case, the employee did not approve the connection and the attackers turned to social engineering tactics. They contacted the employee directly via WhatsApp and claimed to be part of the Uber security team, saying they needed access to the employee's account for audit purposes. This shows the importance of verifying the identity of anyone who requests access to your account or bypassing security measures.
Next time your boss or a colleague is ask you sensible information or access, make sure you are really talking to them!
Lateral Movement
Once the attackers had gained access to the employee's account, they had a clear goal in mind: to access sensitive information in order to deploy ransomware, extort money, or publicly disclose secrets. To achieve this goal, the attacker used the VPN connectivity available from the portal to access Uber's intranet.
Once on the intranet, the attacker scanned the network to discover shared network storage and found PowerShell scripts with hardcoded ADMIN user and password information. With this ADMIN access, the attacker was able to obtain access to multiple major services such as Google Apps, AWS, Slack, and internal applications.
Conclusion
In conclusion, the Uber hack of 2022 serves as a cautionary tale for the importance of strong security practices and the importance of information security within a company. While it is essential for companies to implement strong passwords and robust verification processes, it is also crucial to recognize that even with these measures in place, it can be difficult to prevent a compromised account in a company with thousands of employees. In this case, it appears that a clear file with hard-coded administrator access was available on Uber's network, providing a weak link that the attackers were able to exploit.
To prevent similar attacks in the future, it is crucial for companies to prioritize information security and ensure that all sensitive information is stored securely and access is strictly controlled. By following these best practices, companies can protect themselves and their customers from the consequences of a major security breach.


